Implementing SSL using Wildcard certificate in SAP PO system
Implementing SSL using Wildcard certificate in PO system (wildcard extension .pfx )
A SSL Wildcard certificate is a single certificate with a
wildcard character (*) in the domain name field. This allows the certificate to
secure multiple sub domain names (hosts) pertaining to the same base domain.
The wildcard certificate was provided by the client with the
extension .pfx.
Step 1 - Convert “.pfx” to “*.pse”
sapgenpse import_p12 -p domain.pse
domain.pfx
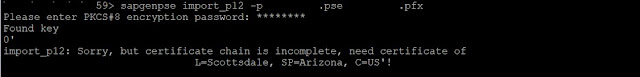
Failed due to unrecognition of root certificate : but
certificate chain is incomplete, need certificate of 'CN= Secure Certificate
Authority , OU=XXXX, O="XXXX", L=XX, SP=XX, C=XX'
Step 2 - Convert pfx to pem first through
openssl command
Note: The
PKCS#12 or PFX format is a binary format for storing the server certificate,
intermediate certificates, and the private key in one encryptable file. PFX
files usually have extensions such as .pfx and .p12. PFX files are typically
used on Windows machines to import and export certificates and private keys.
openssl pkcs12 -in domain.pfx
-nocerts -out domain.pem -nodes
or
openssl pkcs12 -in
certificatename.pfx -out certificatename.pem
Step 3 - Need p7b certificate to extract the
rootCA & SubCA.
So Convert domain.pem to domain.p7b
Note: The PKCS#7 or P7B format is stored
in Base64 ASCII format and has a file extension of .p7b or .p7c.
A P7B file only contains certificates and chain certificates (Intermediate
CAs), not the private key. The most common platforms that support P7B files are
Microsoft Windows and Java Tomcat.
openssl crl2pkcs7 -nocrl
-certfile domain.pem -out domain.p7b
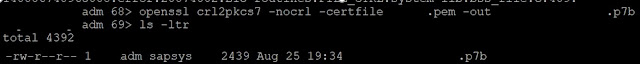
Step 4 - Extract the RootCA , SubCA and host certificate
from p7b with .cer format:

Step – 5 Now again generating PSE from PFX:
<by using the generated root.cer and subCA.cer>
Refer Note : 2148457 - How to convert the
keypair of a PKCS#12 / PFX container into a PSE file
sapgenpse import_p12 -p domain.pse
-r root.cer -r secure.cer domain.pfx
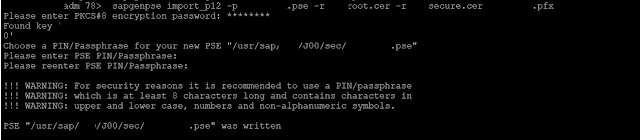
Save without password the pse file.
Step – 6 Replace newly created domain.PSE with
existing SAPSSLS*.PSE
Step – 7 : Apply the certificate and private key on
NWA
Navigate to the portal.:
NWA-> Configuration -> Certificate & keys
SSL_ICM * and SSL_ICM*50001
è
Export the private key and certificate backup before
delete.
è
Delete the existing privatekey and old
certificate in side SSL_ICM_Node
è
Import the pfx file with choosing pkcs12 format
(This will work as a private certificate)
è
Import CSR response for the private certificate
in below sequence: (Which was extracted from the domain.p7b)
1.
Host certificate
2.
Intermediate/ subca cer
3.
Root certificate
è Take the restart of ICM
è
Take the restart of SSL provider service
If SSL is not enabled, kindly take the application restart.
To check the link is secured open the link in IE and click
on lock sign in the browser and check the validity of the certificate.
Reference:
Few more command related to certificate conversion .
If client provide the .cer with the private key then
combined both and generate domain.pfx
Convert CER and Private Key to PFX
openssl pkcs12 -export -in certificatename.cer -inkey privateKey.key
-out certificatename.pfx -certfile cacert.cer
Convert P7B to
PFX
Step 1 - Convert P7B to CER
openssl pkcs7 -print_certs -in certificatename.p7b -out
certificatename.cer
Step 2 - Convert CER and Private Key to PFX
openssl pkcs12 -export -in certificatename.cer -inkey privateKey.key
-out certificatename.pfx -certfile cacert.cer
Convert pfx to PEM
Note: The PKCS#12 or PFX format is a binary format for storing the
server certificate, intermediate certificates, and the private key in one
encryptable file. PFX files usually have extensions such as .pfx and .p12. PFX
files are typically used on Windows machines to import and export certificates
and private keys.
openssl pkcs12 -in certificatename.pfx -out certificatename.pem




Comments
Post a Comment